Hacking the Sprint AIRAVE 2.5 -- Part 1: A Fly on the Wall
Sun 27 March 2022 by bbloughRecently I've taken a deeper interest in hardware, including programming embedded systems, writing Verilog for FPGA devices, and hardware security in general. It's a lot of fun to build things, but it can also be a lot of fun taking things apart or seeing how you can make them fail.
Enter what I've been playing with in my free time for the past week or so: the Sprint AIRAVE 2.5+.
Background
The Sprint AIRAVE is a femtocell. It's used to boost wireless access in areas where coverage is poor. In short, cellular devices connect to the AIRAVE as if it were a cellular tower, and the AIRAVE connects to Sprint's network using a broadband internet connection. From the user perspective, the calls appear to be using the cellular network (as opposed to something like WiFi calling), but in reality, the calls are being sent over the broadband connection to Sprint.
Motivation
Sometime in the past year, I was contacted by Sprint and notified that after a certain date, my AIRAVE would no longer be functional, as they were making changes to the network as part of the T-Mobile merger. That date has come and gone, so my AIRAVE has been sitting on the shelf collecting dust. I figured why not see what makes it tick, and maybe find another use for it. Even if I wind up destroying it in the process, at least there's a chance of reusing it, rather than just sending it off to the landfill.
For anyone interested in playing with these, you may be able to pick one up on eBay or other sites that sell used hardware.
Board Inspection
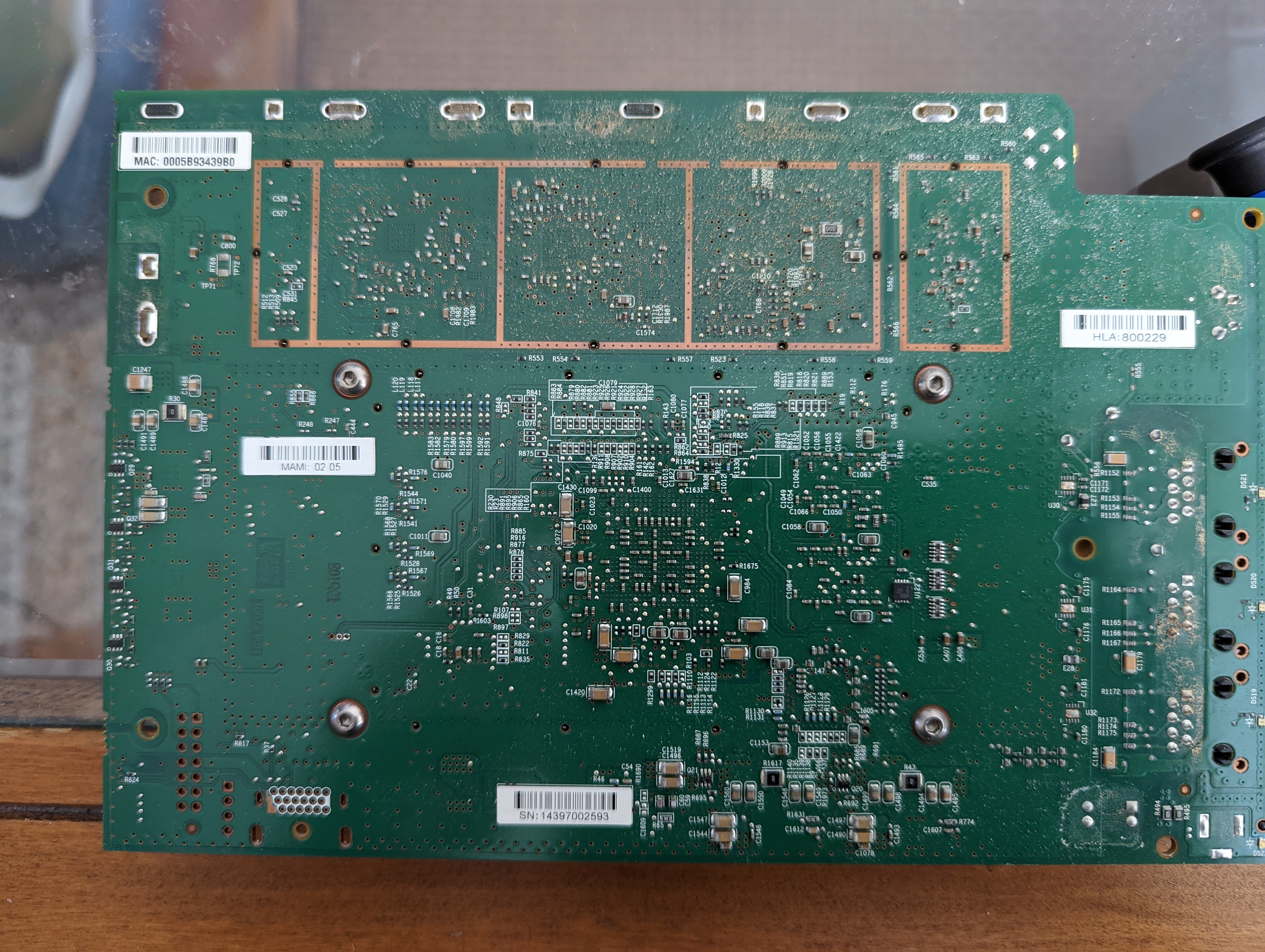
Opening the case and removing the board revealed a large heat sink and a couple of RF-shielded sections.
The RF-shielded areas contain the GPS and cellular radio chips. They're not really important to what I'm trying to do, so I didn't go any further than looking up the part numbers to identify the chips.
Underneath the heat sink is the CPU (marked in blue) and NAND flash (marked in green). The CPU is a Freescale BSC9131 PowerPC, and the NAND flash holds 128MB. Other chips visible are DDR memory (12 o'clock), a thermal watchdog (2 o'clock), line drivers (6 o'clock) and an ethernet controller (11 o'clock).
The back of the board doesn't have much to interest us, except that it's very easy to see some interesting hole patterns in the lower left corner. My understanding is that the 14-pin arrangement may be a JTAG interface, but I haven't attempted to verify this. However, it seemed very likely that the 4-pin array would be a UART interface, so I proceeded with this assumption.
UART Connection
A quick test of the 4-pin array with a digital multimeter identified the ground and 3.3v pins.
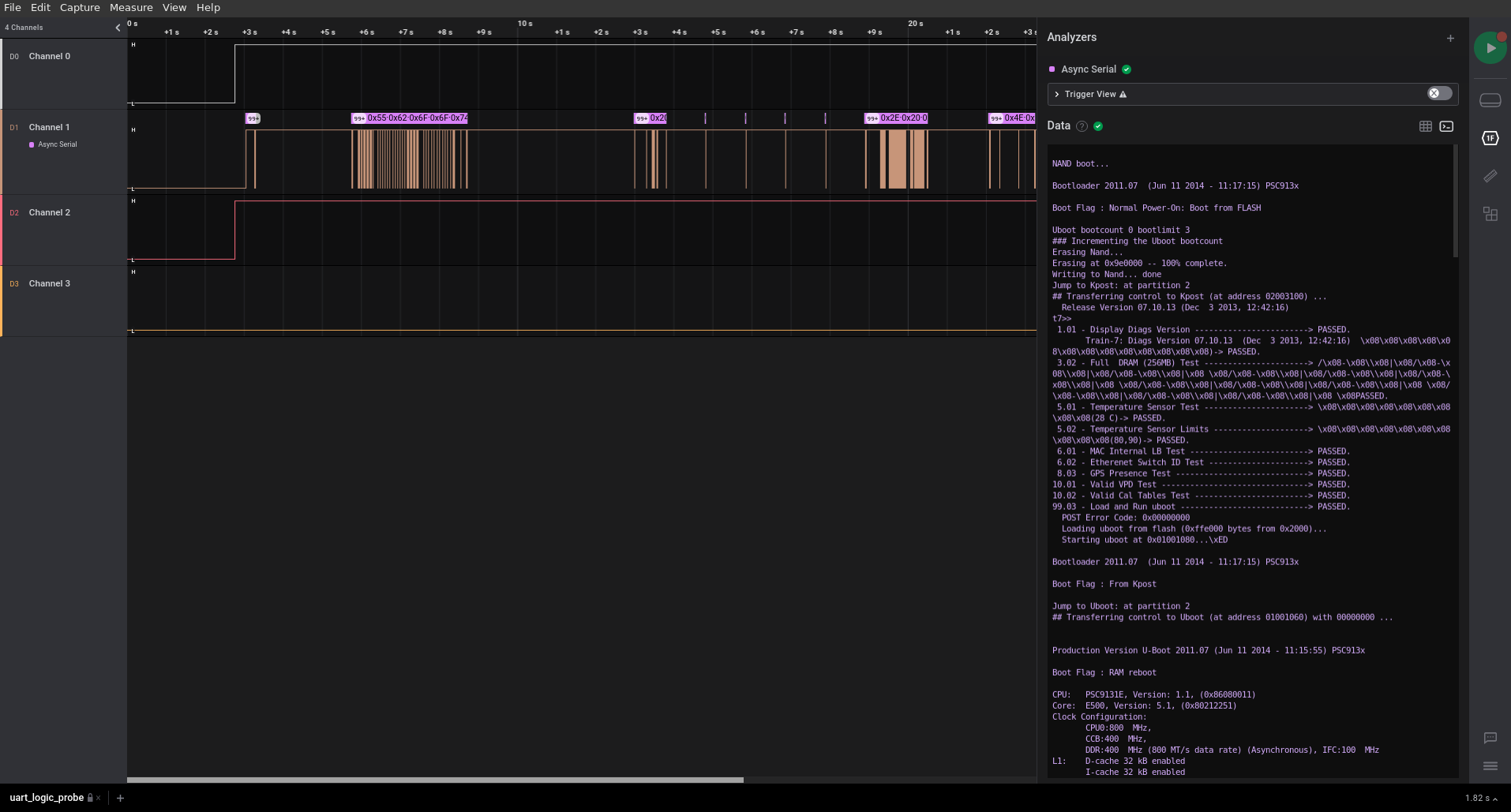
To make things easier, I soldered a header to the UART interface, and connected my Saleae logic analyzer.
Opening Saleae Logic 2, configuring the channels, and booting the AIRAVE made it very easy to identify the TX pin and view the output from the boot process.
With the UART pinout confirmed, the logic levels weren't really needed anymore so I switched to using an Adafruit FT232H breakout board as a UART-to-USB adapter and watched the output using picocom.
NAND boot...
Bootloader 2011.07 (Jun 11 2014 - 11:17:15) PSC913x
Boot Flag : Normal Power-On: Boot from FLASH
Uboot bootcount 0 bootlimit 3
### Incrementing the Uboot bootcount
Erasing Nand...
Erasing at 0x9a0000 -- 33% complete.
Erasing at 0x9c0000 -- 66% complete.
Erasing at 0x9e0000 -- 100% complete.
Writing to Nand... done
Jump to Kpost: at partition 2
## Transferring control to Kpost (at address 02003100) ...
Release Version 07.10.13 (Dec 3 2013, 12:42:16)
t7>>
1.01 - Display Diags Version ------------------------> PASSED.
Train-7: Diags Version 07.10.13 (Dec 3 2013, 12:42:16) )-> PASSED.
3.02 - Full DRAM (256MB) Test ----------------------> /-\|/-\|/-\| /-\|/-\|/-\| /-\|/-\|/-\| /-\|/-\|/-\| PASSED.
5.01 - Temperature Sensor Test ----------------------> (26 C)-> PASSED.
5.02 - Temperature Sensor Limits --------------------> (80,90)-> PASSED.
6.01 - MAC Internal LB Test -------------------------> PASSED.
6.02 - Etherenet Switch ID Test ---------------------> PASSED.
8.03 - GPS Presence Test ----------------------------> PASSED.
10.01 - Valid VPD Test -------------------------------> PASSED.
10.02 - Valid Cal Tables Test ------------------------> PASSED.
99.03 - Load and Run uboot ---------------------------> PASSED.
POST Error Code: 0x00000000
Loading uboot from flash (0xffe000 bytes from 0x2000)...
Starting uboot at 0x01001080...í
Bootloader 2011.07 (Jun 11 2014 - 11:17:15) PSC913x
Boot Flag : From Kpost
Jump to Uboot: at partition 2
## Transferring control to Uboot (at address 01001060) with 00000000 ...
Production Version U-Boot 2011.07 (Jun 11 2014 - 11:15:55) PSC913x
Boot Flag : RAM reboot
CPU: PSC9131E, Version: 1.1, (0x86080011)
Core: E500, Version: 5.1, (0x80212251)
Clock Configuration:
CPU0:800 MHz,
CCB:400 MHz,
DDR:400 MHz (800 MT/s data rate) (Asynchronous), IFC:100 MHz
L1: D-cache 32 kB enabled
I-cache 32 kB enabled
Board: Airvana C5000RDB
Watchdog enabled
I2C: ready
SPI: ready
DRAM: 512 MiB (DDR3, 32-bit, CL=6, ECC off)
L2: 256 KB already enabled
NAND: 128 MiB
In: serial
Out: serial
Err: serial
Net: eTSEC1
Checking WAN link ....
...... TIMEOUT !!
Speed: 100, full duplex
Reset Uboot boot count
bootcount 3 bootlimit 3
### Rolling back to standby image
Erasing Kernel 2 ...
Erasing at 0x3e0000 -- 4% complete.
Erasing at 0x400000 -- 8% complete.
Erasing at 0x420000 -- 13% complete.
Erasing at 0x440000 -- 17% complete.
Erasing at 0x460000 -- 21% complete.
Erasing at 0x480000 -- 26% complete.
Erasing at 0x4a0000 -- 30% complete.
Erasing at 0x4c0000 -- 34% complete.
Erasing at 0x4e0000 -- 39% complete.
Erasing at 0x500000 -- 43% complete.
Erasing at 0x520000 -- 47% complete.
Erasing at 0x540000 -- 52% complete.
Erasing at 0x560000 -- 56% complete.
Erasing at 0x580000 -- 60% complete.
Erasing at 0x5a0000 -- 65% complete.
Erasing at 0x5c0000 -- 69% complete.
Erasing at 0x5e0000 -- 73% complete.
Erasing at 0x600000 -- 78% complete.
Erasing at 0x620000 -- 82% complete.
Erasing at 0x640000 -- 86% complete.
Erasing at 0x660000 -- 91% complete.
Erasing at 0x680000 -- 95% complete.
Erasing at 0x6a0000 -- 100% complete.
Done!
Writing to Nand Dir at 16 ...Done!
Erasing Nand...
Erasing at 0x9a0000 -- 33% complete.
Erasing at 0x9c0000 -- 66% complete.
Erasing at 0x9e0000 -- 100% complete.
Writing to Nand... done
Hit ESC to stop autoboot: 0
partition changed to nand0,9
Tring to load kernel from flash ... Partition Kernel1:
No Valid Kernel on flash
### JFFS2 loading 'boot.bin' to 0x2000000
Scanning JFFS2 FS: . . . . . . . . . . . . . . done.
### JFFS2 load complete: 1939741 bytes loaded to 0x2000000
bootcount 0 bootlimit 3
### Incrementing the bootcount
Erasing Nand...
Erasing at 0x9a0000 -- 33% complete.
Erasing at 0x9c0000 -- 66% complete.
Erasing at 0x9e0000 -- 100% complete.
Writing to Nand... done
## Booting kernel from Legacy Image at 02000000 ...
Image Name: Femto C4000 Kernel Image
Created: 2014-05-21 5:11:53 UTC
Image Type: PowerPC Linux Multi-File Image (gzip compressed)
Data Size: 1939677 Bytes = 1.8 MiB
Load Address: 00000000
Entry Point: 00000000
Contents:
Image 0: 1895127 Bytes = 1.8 MiB
Image 1: 330 Bytes = 330 Bytes
Image 2: 9897 Bytes = 9.7 KiB
Image 3: 9897 Bytes = 9.7 KiB
Image 4: 11997 Bytes = 11.7 KiB
Image 5: 12389 Bytes = 12.1 KiB
Verifying Checksum ... OK
## Loading init Ramdisk from multi component Legacy Image at 02000000 ...
Using Train 7 dtb in boot.bin
## Flattened Device Tree from multi component Image at 02000000
Booting using the fdt at 0x21d39d8
Uncompressing Multi-File Image ... OK
Loading Device Tree to 03ffa000, end 03fffedc ... OK
Using PSC9131 RDB machine description
Memory CAM mapping: 256/64 Mb, residual: 0Mb
Linux version 2.6.33.9-rt31 (sbindagi@linuxws18.swlab.wirelessworld.airvananet.com) (gcc version 4.3.2 (GCC) ) #32 SMP Wed May 21 01:11:31 EDT 2014
CPU maps initialized for 1 thread per core
bootconsole [udbg0] enabled
setup_arch: bootmem
psc913x_board_setup_arch()
psc913x board from Freescale Semiconductor
arch: exit
Zone PFN ranges:
DMA 0x00000000 -> 0x00014000
Normal 0x00014000 -> 0x00014000
HighMem 0x00014000 -> 0x00014000
Movable zone start PFN for each node
early_node_map[1] active PFN ranges
0: 0x00000000 -> 0x00014000
MMU: Allocated 1088 bytes of context maps for 255 contexts
PERCPU: Embedded 7 pages/cpu @c0672000 s4272 r8192 d16208 u65536
pcpu-alloc: s4272 r8192 d16208 u65536 alloc=16*4096
pcpu-alloc: [0] 0
Built 1 zonelists in Zone order, mobility grouping on. Total pages: 81280
Kernel command line: root=/dev/mtdblock9 rw rootfstype=jffs2 mem=0x14000000 init=/init console=ttyS1,115200 HOSTNAME=picasso PRIPART=4
PID hash table entries: 2048 (order: 1, 8192 bytes)
Dentry cache hash table entries: 65536 (order: 6, 262144 bytes)
Inode-cache hash table entries: 32768 (order: 5, 131072 bytes)
Memory: 320384k/327680k available (3668k kernel code, 7088k reserved, 184k data, 161k bss, 180k init)
Kernel virtual memory layout:
* 0xfffc1000..0xfffff000 : fixmap
* 0xffc00000..0xffe00000 : highmem PTEs
* 0xffbfe000..0xffc00000 : early ioremap
* 0xd5000000..0xffbfe000 : vmalloc & ioremap
Registering Sched Trace sysrq handler
Hierarchical RCU implementation.
NR_IRQS:512 nr_irqs:512
mpic: Setting up MPIC " OpenPIC " version 1.2 at ff740000, max 1 CPUs
mpic: ISU size: 256, shift: 8, mask: ff
mpic: Initializing for 256 sources
clocksource: timebase mult[5000000] shift[22] registered
Console: colour dummy device 80x25
Mount-cache hash table entries: 512
Brought up 1 CPUs
NET: Registered protocol family 16
tdm_init
FSL_GUTS setting AIC SPI
Local Access Window Configuration
LAWBAR00: 0x00000000 LAWAR00: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR01: 0x00000000 LAWAR01: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR02: 0x00000000 LAWAR02: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR03: 0x00000000 LAWAR03: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR04: 0x00000000 LAWAR04: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR05: 0x00000000 LAWAR05: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR06: 0x00000000 LAWAR06: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR07: 0x00000000 LAWAR07: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR08: 0x00000000 LAWAR08: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR09: 0x00000000 LAWAR09: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR10: 0x00000000 LAWAR10: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
LAWBAR11: 0x00000000 LAWAR11: 0x00000000 (EN: 0 TGT: 0x00 SIZE: 0)
bio: create slab <bio-0> at 0
Switching to clocksource timebase
NET: Registered protocol family 2
IP route cache hash table entries: 4096 (order: 2, 16384 bytes)
TCP established hash table entries: 16384 (order: 5, 131072 bytes)
TCP bind hash table entries: 16384 (order: 5, 131072 bytes)
TCP: Hash tables configured (established 16384 bind 16384)
TCP reno registered
UDP hash table entries: 256 (order: 1, 8192 bytes)
UDP-Lite hash table entries: 256 (order: 1, 8192 bytes)
NET: Registered protocol family 1
RPC: Registered udp transport module.
RPC: Registered tcp transport module.
RPC: Registered tcp NFSv4.1 backchannel transport module.
fsl-ifc ff71e000.ifc: Freescale Integrated Flash Controller
HugeTLB registered 4 MB page size, pre-allocated 0 pages
HugeTLB registered 16 MB page size, pre-allocated 0 pages
HugeTLB registered 64 MB page size, pre-allocated 0 pages
HugeTLB registered 256 MB page size, pre-allocated 0 pages
HugeTLB registered 1 GB page size, pre-allocated 0 pages
JFFS2 version 2.2. (NAND) © 2001-2006 Red Hat, Inc.
msgmni has been set to 626
alg: No test for stdrng (krng)
io scheduler noop registered
io scheduler deadline registered
io scheduler cfq registered (default)
Generic non-volatile memory driver v1.1
Serial: 8250/16550 driver, 2 ports, IRQ sharing enabled
serial8250.0: ttyS0 at MMIO 0xff704500 (irq = 18) is a 16550A
serial8250.0: ttyS1 at MMIO 0xff704600 (irq = 18) is a 16550A
console [ttyS1] enabled, bootconsole disabled
console [ttyS1] enabled, bootconsole disabled
brd: module loaded
loop: module loaded
8323 Xilinx FPGA Loader Driver v1.0
Airvana Reset Driver v1.0
reset: Reset IRQ 17
reset: PPS IRQ 19
reset: GPIO Reset 197
reset: GPIO PPS 198
Airvana GPIO LEDS Loader Driver v1.0
NAND ECC MODE 2
NAND device: Manufacturer ID: 0xc2, Chip ID: 0xf1 (Unknown NAND 128MiB 3,3V 8-bit)
Scanning device for bad blocks
NOHZ: local_softirq_pending 100
NOHZ: local_softirq_pending 100
cmdlinepart partition parsing not available
RedBoot partition parsing not available
Creating 12 MTD partitions on "ff800000.flash":
0x000000000000-0x000000100000 : "Bootloader"
0x000000100000-0x0000003e0000 : "Kern1"
0x0000003e0000-0x0000006c0000 : "Kern2"
0x0000006c0000-0x000000700000 : "Dir"
0x000000700000-0x000000760000 : "VPD"
0x000000760000-0x000000860000 : "Uboot1"
0x000000860000-0x000000960000 : "Uboot2"
0x000000960000-0x0000009a0000 : "HWCW"
0x0000009a0000-0x000000a00000 : "Env"
0x000000a00000-0x000003a00000 : "Kernel-RootFS-A"
0x000003a00000-0x000006a00000 : "Kernel-RootFS-B"
0x000006a00000-0x000008000000 : "FlashFS"
fsl,ifc-nand ff800000.nand: IFC NAND device at 0xff800000, bank 0
fsl-espi ff707000.spi: Freescale eSPI Controller driver at 0xd5102000 (irq = 22)
of_spi found radioc
fsl-espi ff706000.spi: Freescale eSPI Controller driver at 0xd5106000 (irq = 23)
fsl-espi ff70e000.spi: Freescale eSPI Controller driver at 0xd510a000 (irq = 24)
of_spi found radioa
fsl-espi ff70d000.spi: Freescale eSPI Controller driver at 0xd510e000 (irq = 25)
of_spi found radiob
of_spi found dac
CurieDSP fake phy: Registered new driver
Fixed MDIO Bus: probed
/proc/ptp_1588 created
IEEE1588: ptp-timer device present in the system
IEEE1588: ptp-timer initialized
nic0: Gianfar Ethernet Controller Version 1.4-skbr1.1.5, 00:05:b9:34:39:b0
nic0: Running with NAPI enabled
nic0: RX BD ring size for Q[0]: 128
nic0: RX BD ring size for Q[1]: 128
nic0: RX BD ring size for Q[2]: 128
nic0: RX BD ring size for Q[3]: 128
nic0: RX BD ring size for Q[4]: 128
nic0: RX BD ring size for Q[5]: 128
nic0: RX BD ring size for Q[6]: 128
nic0: RX BD ring size for Q[7]: 128
nic0: TX BD ring size for Q[0]: 128
nic0: TX BD ring size for Q[1]: 128
nic0: TX BD ring size for Q[2]: 128
nic0: TX BD ring size for Q[3]: 128
nic0: TX BD ring size for Q[4]: 128
nic0: TX BD ring size for Q[5]: 128
nic0: TX BD ring size for Q[6]: 128
nic0: TX BD ring size for Q[7]: 128
Freescale PowerQUICC MII Bus: probed
i2c /dev entries driver
lm75 0-004a: hwmon0: sensor 'lm75'
PowerPC Book-E Watchdog Timer Loaded
PowerPC Book-E Watchdog Timer Enabled (wdt_period=32)
<6>mknod tdm c 239 0
tdm_dev_init: registering the character device adap 0
tdm_fsl_starlite: Freescale Starlite TDM Driver Adapter:Init
TCP cubic registered
Initializing XFRM netlink socket
NET: Registered protocol family 17
NET: Registered protocol family 15
Distributed Switch Architecture driver version 0.1
nic0[0]: detected a Marvell 88E6071 switch
dsa slave smi: probed
NOHZ: local_softirq_pending 100
NOHZ: local_softirq_pending 100
NOHZ: local_softirq_pending 100
NOHZ: local_softirq_pending 100
NOHZ: local_softirq_pending 100
NOHZ: local_softirq_pending 100
NOHZ: local_softirq_pending 100
NOHZ: local_softirq_pending 100
Empty flash at 0x02bd47e0 ends at 0x02bd4800
Empty flash at 0x02bd9940 ends at 0x02bda000
VFS: Mounted root (jffs2 filesystem) on device 31:9.
Freeing unused kernel memory: 180k init
Empty flash at 0x009a80bc ends at 0x009a8800
jffs2_scan_inode_node(): CRC failed on node at 0x00c457c8: Read 0xffffffff, calculated 0x998a0dd1
Empty flash at 0x00c459e0 ends at 0x00c46000
Empty flash at 0x014a3020 ends at 0x014a3800
Found SPI DAC, initializing
Running /init
FEMTO BOARD PROFILE:410100
/sbin/watchdog -t 1 /dev/watchdog ok
FIRMWARE VERSION 6.5.02.02005
Corefiles wont get generated
To enable crash daemon, please run crashdaemon_install.sh
to configure the ftp server to upload the core file
Starting SysInit
Setting clock : Thu Jan 1 00:00:08 UTC 1970 [ OK ]
Starting system logger: [ OK ]
Starting kernel logger: [ OK ]
## Error: "kposterr" not defined
Updates user information
Changing password for 0005B9-cdmaFAP3-0005B93439B0
Password for 0005B9-cdmaFAP3-0005B93439B0 changed by root
Checking Uboot upgrade....
ubootupgrade: start
GetAllVpdData: EEPROM values : Checksum -2035027229 Major 2 Minor 1
Upgrade Kernel Femto C4000 Kernel Image 2014-05-21 5:11:53 UTC at /dev/mtd1
ubootupgrade: **************************************
ubootupgrade: Update Kernel dev /dev/mtd1
ubootupgrade: **************************************
ubootupgrade: execute cmd flash_eraseall /dev/mtd1
Erasing 128 Kibyte @ 0 -- 0 % complete.
Erasing 128 Kibyte @ 20000 -- 4 % complete.
Erasing 128 Kibyte @ 40000 -- 8 % complete.
Erasing 128 Kibyte @ 60000 -- 13 % complete.
Erasing 128 Kibyte @ 80000 -- 17 % complete.
Erasing 128 Kibyte @ a0000 -- 21 % complete.
Erasing 128 Kibyte @ c0000 -- 26 % complete.
Erasing 128 Kibyte @ e0000 -- 30 % complete.
Erasing 128 Kibyte @ 100000 -- 34 % complete.
Erasing 128 Kibyte @ 120000 -- 39 % complete.
Erasing 128 Kibyte @ 140000 -- 43 % complete.
Erasing 128 Kibyte @ 160000 -- 47 % complete.
Erasing 128 Kibyte @ 180000 -- 52 % complete.
Erasing 128 Kibyte @ 1a0000 -- 56 % complete.
Erasing 128 Kibyte @ 1c0000 -- 60 % complete.
Erasing 128 Kibyte @ 1e0000 -- 65 % complete.
Erasing 128 Kibyte @ 200000 -- 69 % complete.
Erasing 128 Kibyte @ 220000 -- 73 % complete.
Erasing 128 Kibyte @ 240000 -- 78 % complete.
Erasing 128 Kibyte @ 260000 -- 82 % complete.
Erasing 128 Kibyte @ 280000 -- 86 % complete.
Erasing 128 Kibyte @ 2a0000 -- 91 % complete.
Erasing 128 Kibyte @ 2c0000 -- 95 % complete.
Erasing 128 Kibyte @ 2e0000 -- 100% complete.
ubootupgrade: execute cmd nandwrite -q -p /dev/mtd1 /boot.bin
ubootupgrade: Dir update sucessful
Generating dropbear rsa key
Generating dropbear dss key
Start SSH server ....
Starting VortiQa UTM.
Starting VortiQa ...
VortiQa-Phase3-0831-Patch5-11092011-QoS
ln: /usr/lib/libiips_wrap.so: File exists
cat: can't open '/proc/sys/net/ipv6/conf/all/forwarding': No such file or directory
Entry Success in IkeBaseModuleInit(306)
Entry Success in IkeBaseModuleInit(320)
Entry Success in IkeBaseInitialize(74)
Entry Success in IkeBaseInitStaticAlloc(163)
Entry Success in IkeBaseInitialize(84)
Entry Success in IkeBaseInitDataStructures(217)
Exit Success in IkeBaseInitDataStructures(241)
Entry Success in IkeBaseInitialize(94)
Entry Success in IkeBaseInitialize(112)
Exit Success in IkeBaseInitialize(122)
Entry Success in IkeBaseModuleInit(328)
Entry Success in IkeBaseModuleInit(339)
Entry Success in IkeCmnInit(148)
Entry Success in IkeCmnInit(178)
Entry Success in IkeCmnInit(200)
Entry Success in IkeCmnInit(203)
Entry Success in IkeCmnInit(214) :: Before calling IkeCmnIfaceSockInit()
Entry Success in IkeCmnIfaceSockInit(1271)
Exit Success in IkeCmnIfaceSockInit(1364)
Entry Success in IkeCmnInit(224) :: After calling IkeCmnIfaceSockInit()
Entry Success in IkeBaseInitialize(74)
Entry Success in IkeBaseInitStaticAlloc(163)
Entry Success in IkeBaseInitialize(84)
Entry Success in IkeBaseInitDataStructures(217)
Exit Success in IkeBaseInitDataStructures(241)
Entry Success in IkeBaseInitialize(94)
Entry Success in IkeBaseInitialize(112)
Exit Success in IkeBaseInitialize(122)
Entry Success in IkeBaseInitialize(74)
Entry Success in IkeBaseInitStaticAlloc(163)
Entry Success in IkeBaseInitialize(84)
Entry Success in IkeBaseInitDataStructures(217)
Exit Success in IkeBaseInitDataStructures(241)
Entry Success in IkeBaseInitialize(94)
Entry Success in IkeBaseInitialize(112)
Exit Success in IkeBaseInitialize(122)
Entry Success in IkeBaseInitialize(74)
Entry Success in IkeBaseInitStaticAlloc(163)
Entry Success in IkeBaseInitialize(74)
Entry Success in IkeBaseInitStaticAlloc(163)
Entry Success in IkeBaseInitialize(84)
Entry Success in IkeBaseInitDataStructures(217)
Exit Success in IkeBaseInitDataStructures(241)
Entry Success in IkeBaseInitialize(94)
Entry Success in IkeBaseInitialize(112)
Exit Success in IkeBaseInitialize(122)
Entry Success in IkeBaseInitialize(84)
Entry Success in IkeBaseInitDataStructures(217)
Exit Success in IkeBaseInitDataStructures(241)
Entry Success in IkeBaseInitialize(94)
Entry Success in IkeBaseInitialize(112)
Exit Success in IkeBaseInitialize(122)
Entry Success in IkeBaseModuleInit(369)
Exit Success in IkeBaseModuleInit(397)
Entry Success in main(122)
Entry Success in main(133)
done
Cannot set device generic segmentation offload settings: No such device
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_adv_win_scale = -2
net.ipv4.conf.all.log_martians = 1
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.accept_source_route = 0
net.ipv4.icmp_echo_ignore_broadcasts = 1
kernel.panic = 60
kernel.pid_max = 10000
net.ipv4.ip_local_port_range = 62001 65535
net.core.rmem_max = 110592
net.core.rmem_default = 110592
net.core.wmem_max = 110592
net.core.wmem_default = 110592
kernel.sched_trace = 0
kernel.sched_rttrap = 0
kernel.sched_rttrap_delay = 50
vm.min_free_kbytes = 20000
vm.panic_on_oom = 1
*********************************************************
ATTENTION : Temporary Vortiqa configuration changes !!!
*********************************************************
***********************************************************************************************
Welcome to the [1;31m[0m Command Line Interface
***********************************************************************************************
iGateway:/>iGateway:/config/iapd/policy>iGateway:/config/iapd/policy>iGateway:/config/algs>Disabled Alg For v4sipudp
iGateway:/config/algs>iGateway:/config/ad/timer>iGateway:/config/ad/timer>
Default TimeOuts
****************
General Timeout : 60
DefaultTcp : 600
DefaultUdp : 60
DefaultIcmp : 4
TcpPreConnEstb : 30
tcpresetval : 20
Timer Name Protocol Port TimeOut
*********************************************************
ftpinac TCP 21 600
hainac TCP 15000 60000
dnsinac UDP 53 30
iGateway:/config/ad/timer>iGateway:/config/logmsgs/throttling>iGateway:/config/logmsgs/throttling>iGateway:/config/logmsgs/throttling>iGateway:/config/logmsgs/throttling>Throttle Count: : 10000
Throttle Time: : 40
Issue Mask
_______________
iGateway:/config/logmsgs/throttling>Throttle Count: : 10000
Throttle Time: : 20
Issue Mask
_______________
iGateway:/config/logmsgs/throttling>Throttle Count: : 10000
Throttle Time: : 20
Issue Mask
_______________
iGateway:/config/logmsgs/throttling>Not in Context
*************************************************
Goodbye! Hope you had good time!!
*************************************************
����������Finished rcS
*****PROCMON: Starting the scriptProcMon Process id for shortLong is 1447
**PROCMON**:1970-01-01 00:00:47.884: Invoking killall.
**PROCMON**:1970-01-01 00:00:47.885: Starting up all processes
***PROCMON***: Inside PidLink::start
***PROCMON***: Inside PidLink::start
***PROCMON**: Outside while in start
***PROCMON***: Inside PidLink::start
***PROCMON**: Outside while in start
***PROCMON***: Inside PidLink::start
***PROCMON**: Outside while in start
***PROCMON***: Inside PidLink::start
***PROCMON**: Outside while in start
***PROCMON***: Inside PidLink::start
***PROCMON***: Inside PidLink::start
***PROCMON**: Outside while in start
***PROCMON***: Inside PidLink::start
**PROCMON**:1970-01-01 00:01:45.005: done with starting all processes
***** PROCMON: Starting fdleak script *****
**PROCMON**:1970-01-01 00:01:45.015: Beginning monitoring of all processes.
NOT monitoring fds. touch /conf_files/fdcheck to enable
**PROCMON**: Monitoring processes now!!
The boot output gave a lot of detail about the system, including the CPU and speed, amount of RAM, flash layout, and Linux kernel version. However, there was no login prompt, nor did it allow me to stop the Uboot process and get a Uboot shell. So at this point, all I could do was watch the boot, but not interact. Fortunately, there are sometimes ways around this, which I'll write about in my next post.
sudo reboot
Benjy: The best-laid plans of mice...
Arthur: And men.
Frankie: What?
Arthur: Best-laid plans of mice and men.
Benjy: What have men got to do with it?
-- The Hitchhiker's Guide to the Galaxy TV series
Last year, my intent had been to post monthly updates with details of the F …
read moreFree Software Activities (August 2019)
Debian
-
Fixed bug 933422: passwordsafe — Switch to using wxgtk3
Versions:
- unstable/testing: 1.06+dfsg-3
-
Upgraded passwordsafe package to latest upstream version (1.08.2)
Versions:
- unstable/testing: 1.08.2+dfsg-1
- buster-backports: 1.08.2+dfsg-1~bpo10+1
-
Updated python-django-cas-client to latest upstream version (1.5.1) and did …