NSA Codebreaker Challenge 2015: Background and Task 1
Thu 28 April 2016 by bbloughLast year, the National Security Agency held a reverse engineering competition for students. It ran from September 1st to December 31st, and consisted of four tasks. The results page lists the participating schools and students, along with tasks completed, rankings, and times. I represented Florida State University and was able to complete all four tasks in just under 53 hours.
Background Story
NSA has discovered that the leadership of a terrorist organization is using
a new method of communicating secret messages to its operatives in the
field. Intelligence suggests that each member of the organization is
provided a program that can be used to read the messages, and that a
customized cryptographic implementation is used to generate a
public/private key pair, which is then used to authenticate messages from
leadership to each member.
A copy of the program belonging to a high-ranking operative has been
recovered, along with that individual's key and a text file believed to
contain a hidden message. At first glance, the program appears to simply
check stock information, but this is likely a ruse to make it appear
innocuous. Your mission is to reverse-engineer this software and develop
capabilities to exploit the secret messaging component. There are 4
different tasks for you to complete, with each increasing in difficulty and
building off the previous task(s).
Task 1
We need your help with decoding the message that we've captured. The text
file, key file, and secret messaging program can be found below. The main
objective for this task is to figure out how to decode the message with the
program and report back on your findings.
To complete this task, you will most likely need to analyze the program
binary in order to determine how to trigger the hidden functionality and
decode the secret message.
As stated in the background story, the program appeared to be a simple stock price query utility:
user@host:~/nsa_codebreaker_2015/task_1$ ./codebreaker3 --help
Help:
--debug true : Show debugging information
--help : Show this help message
--symbol <symbol> : The ticker symbol to reference
--action <action> :
'open' for the days opening price
'low' for the days lowest price
'high' for the days highest price
'last' for the last price
--symbol and --action are required arguments
Stock Information Powered by Yahoo!
And indeed, it seemed to work as such:
user@host:~/nsa_codebreaker_2015/task_1$ ./codebreaker3 --symbol GOOG --action open
'open' info for 'GOOG': 708.26
The first order of business was to discover how to invoke the secret functionality.
Running strings on the binary "revealed" something interesting - a hidden option!
--reveal : Enter secret message mode
However, trying that option produced an error:
user@host:~/nsa_codebreaker_2015/task_1$ ./codebreaker3 --reveal
Failed binary name check
At that point, I decided to step through execution in gdb, in order to see what was happening. As it turns out, there is a check that the binary name is exactly 16 characters long
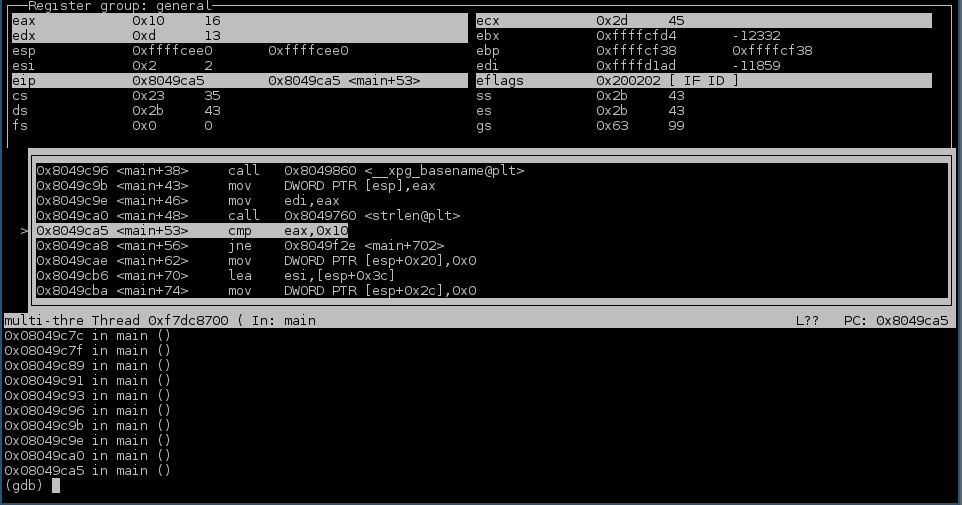
Renaming the binary to be 16 characters long didn't change the error message. So, proceeding
further in gdb with the renamed binary, I found a check that verifies that the
program was invoked as secret-messenger
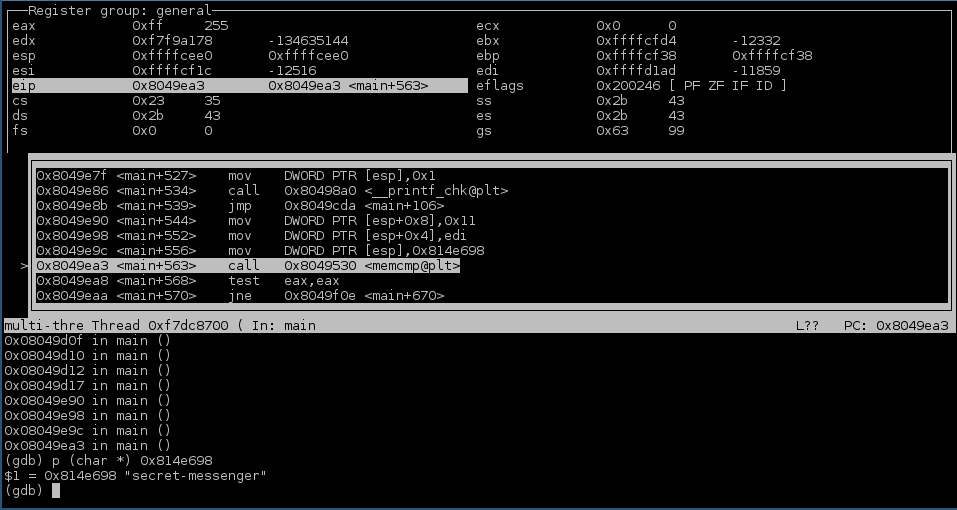
Renaming the binary to secret-messenger was all it took to get further.
user@host:~nsa_codebreaker_2015/task_1$ ./secret-messenger --reveal
Missing required parameter. Run with --help for more info.
The --help text was the same as before, and the output of strings didn't
show any additional options. Rather than diving back into gdb, I decided to
follow the hunch that the existing options served a purpose in the secret mode
as well. A little trial-and-error was called for.
user@host:~nsa_codebreaker_2015/task_1$ ./secret-messenger --reveal --symbol foo --action bar
Could not open 'bar'
access: No such file or directory
So I passed the key file as the action
user@host:~nsa_codebreaker_2015/task_1$ ./secret-messenger --reveal --symbol foo --action tier1_key.pem
Could not open 'foo'
access: No such file or directory
And also the message file as the symbol
user@host:~nsa_codebreaker_2015/task_1$ ./secret-messenger --reveal --symbol tier1_msg.txt --action tier1_key.pem
Could not open 'foo'
Invalid (failed check 1)
Since there was no guarantee that I guessed right the first time, I thought it might be possible that I had the files matched to the wrong arguments. So I tried swapping them
user@host:~nsa_codebreaker_2015/task_1$ ./secret-messenger --reveal --action tier1_msg.txt --symbol tier1_key.pem
*****SIGNATURE IS VALID*****
Message: Meet at 22:00 tomorrow at our secure location. Come alone, and do not tell anyone - this meeting is sensitive, as leadership will be present. To authenticate yourself, mention the pass code osb4rfmthy5dp22kd7qm at the door.
*****SIGNATURE IS VALID*****
And bingo! The action argument went with the message file, while the symbol argument went with the key file.
With the message decoded, Task 1 was complete.